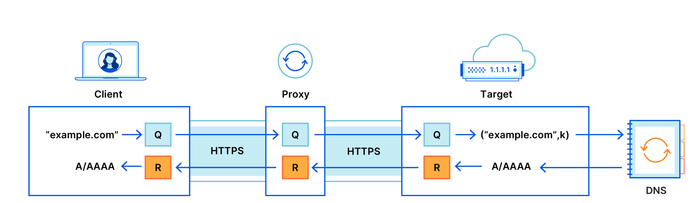
Cloudflare, Apple and Fastly have partnered to develop and begin the technology standardization process ODoH (Oblivious DNS over HTTPS) with the implementation of the DNS over HTTPS option, which preserves the user’s privacy and does not allow the resolver to know his IP- the address. One of the problems with DNS and DNS over HTTPS is data leakage due to the ability of the DNS server to match the requests it sends to the user’s IP address. Since the client sends requests directly, the DNS server initially knows its IP address and all domains that the user is trying to access.
To solve this problem, ODoH additionally introduces an intermediate node – a proxy that redirects client requests to DNS server and broadcasts the responses through itself. Requests and responses are additionally encrypted using public keys, which prevents proxies from detecting content or spoofing DNS messages. Thus, the proxy knows the user’s IP address, but cannot determine which domains the user is requesting. For its part, the DNS server sees the requested domains (it can decrypt the request and send an encrypted response), but does not know who requested them, since all requests come from the general IP address of the proxy.
The changes required to support ODoH in the client are reduced to adding an additional encryption layer to hide traffic from the proxy. In addition to standard TLS encryption, which is used to protect against transit interception during MiTM attacks, authenticated end-to-end encryption of messages between the client and the server, based on the mechanism HPKE (Hybrid Public Key Encryption). The client receives the public key for encryption via DNS (with DNSSEC verification) in one of the fields with additional resources. Using this key allows the DNS server to decrypt client requests. Keys for encrypting the response are generated each time by the client and sent inside the request encrypted with the public key.