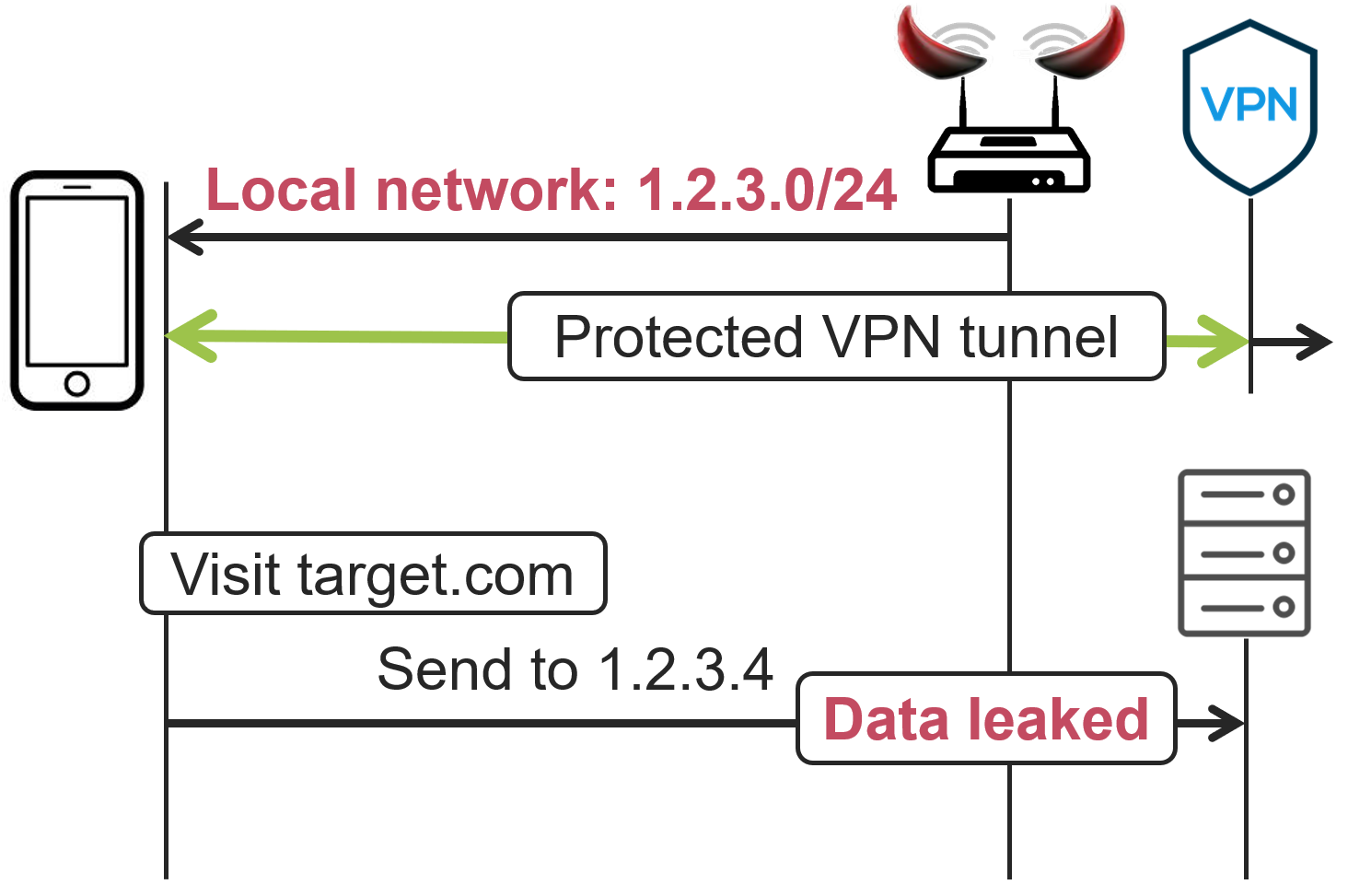
A group of researchers from New York University has developed two methods of attack on VPN, known as tunnelcrack. These vulnerabilities allow attackers who control the wireless access point or the local network of the victim to redirect requests to the target host to their own server, bypassing the VPN tunnel. This kind of attack can occur when connected through an untrusted internet provider or a compromised wireless network. Consequently, the attacker can intercept user traffic, except for connections established through HTTPS which remain protected.
The researchers have identified the following methods of attack:
- localnet (CVE-2023-36672, CVE-2023-35838) – This method exploits the fact that most VPN clients allow direct access to the local network. The attacker-controlled gateway assigns the victim an IP address from the subnet where the target host is located. As a result, the network stack of the victim’s system believes that the host is within reach and directs traffic directly to the attacker’s gateway, bypassing the VPN. For example, if the attacker wants to intercept traffic to the Target.com website with IP address 1.2.3.4, they assign the victim an IP address within the range 1.2.3.0/24. If the VPN client allows direct access to the local network, the victim’s request to 1.2.3.4 would go directly to the attacker’s host.

- serverip (CVE-2023-36673,
/Reports, release notes, official announcements.