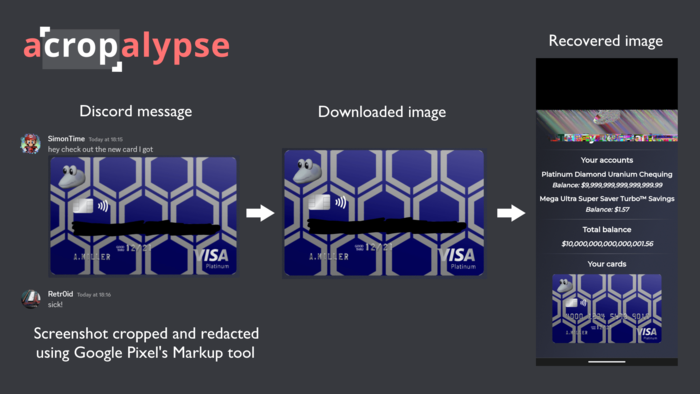
Google Pixel smartphones have been found to have a vulnerability in their Markup application that allows partially restored cut or edited information. The issue, CVE-2023-21036, arises while editing PNG images in the Markup tool. When a new image is recorded, the data is superimposed on the old file without truncation, so the final file received after editing includes the tail of the source file with old compressed data. This creates a problem as users can publish edited images with previously cut-out confidential data that remains in the file unnoticed.
Vulnerability starts from the Google Pixel 3 series smartphones using Android 10 firmware and newer releases. However, the issue has been resolved in the March update Android Carriage for Pixel smartphones, which covers relatively fresh models. Acropalypse.app and an example of a Python script by Buchanan314 can be used to restore the remaining data.
According to reports, the change in the method PARCELFILEDESCRIPTOR.PARSEMODE() is behind the problem. In previous versions, the Android 10 flag “W” (WRITE) caused the charges of the file records to an existing file. However, from the release of Android 10, the behavior changed such that the flag “wt” (Write, truncate) was required to truncate, and when “W” was not removed after the re-recorded.
It is essential to address this vulnerability to ensure that users’ confidential data remains safe when using the Markup tool.