On January 30 at 18:20 (MSK), users experienced a massive failure in determining the hosts in the domain zone ru. This failure was caused by an error during the process of changing keys used to assure the reliability of the RU zone through dnssec. As a result, all domains in the “.ru” zone could not be determined. However, this problem only affected users who used DNS-sores or public DNS services, such as 8.8.8.8, which verify the reliability of requests using DNSSEC. Users of DNS-risolvers, on which DNSSEC is disabled, did not experience any issues.
This incident bears resemblance to last year’s incident with the Internet registrar responsible for the domain zone “nz”. In that case, there was a malfunction in the permission of domain names in the “.nz” zone due to an error during the rotation of the KSK-Signing key used for a digital signature of DNSKEY records. The error was associated with a change in the format of the keys when switching to a new information system of the registrar. The causes of the recent incident in the RU zone have not yet been detailed. The RU domain coordination center has only confirmed in general terms that the problem is related to the reconfiguration of DNSSEC.
Based on external manifestations, it appears that the failure occurred as a result of an attempt to replace the key used to verify the RU zone. This key is the root for other keys used in second-level domains, and it uses the domain key as a higher confirmation of trust. On January 26, an additional key with the identifier 52263 was added to the DNSEC settings of the RU zone in addition to the main key with the identifier 44301.
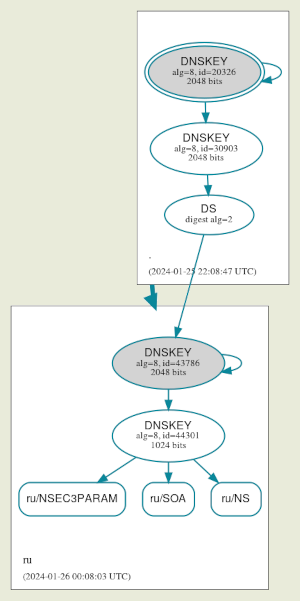
Yesterday, at approximately 18:20, the new key was introduced into the verification process of records in the RU zone. However, due to an error, the authenticity check stopped taking place.