HEANDAI IONIQ SEL CALL published a series of articles with a story how he managed to make changes to the firmware used in the information and entertainment system (IVI) based on the D-Audio2V operating system used in Hyundai and Kia cars. It turned out that all the data necessary for decoding and verification are publicly available on the network and only a few requests in Google were required to determine them.
The firmware update proposed by the manufacturer was supplied in a ZIP file encrypted with a password, and the contents of the firmware itself were encrypted using the AES-CBC algorithm and certified by a digital signature based on the RSA keys. Password from ZIP archiva and AES-key to deciphering the image Updateboot.img managed to find in the Linux_envsetup.sh script, which was in the open form in the System_package components D-Audio2v, distributed to manufacturer of the IVI system.

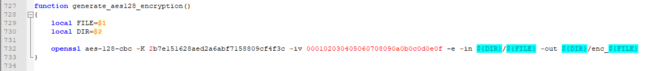
Nevertheless, there was not enough closed key used to certify the digital signature to modify the firmware. It is noteworthy that the RSA key helped to find the Google search engine. The researcher sent a search query, indicating the previously found Aes-key and came across that the key is not unique and is mentioned in the document NIST SP800-38A . Reasoning that the researcher found an open key in the same way, and the RSA-key key was borrowed in a similar way and tried to find information on it in Google. The request showed that the indicated open key is mentioned in the example of one of the guides on the use of Opensl, in which also The closed key is also indicated.
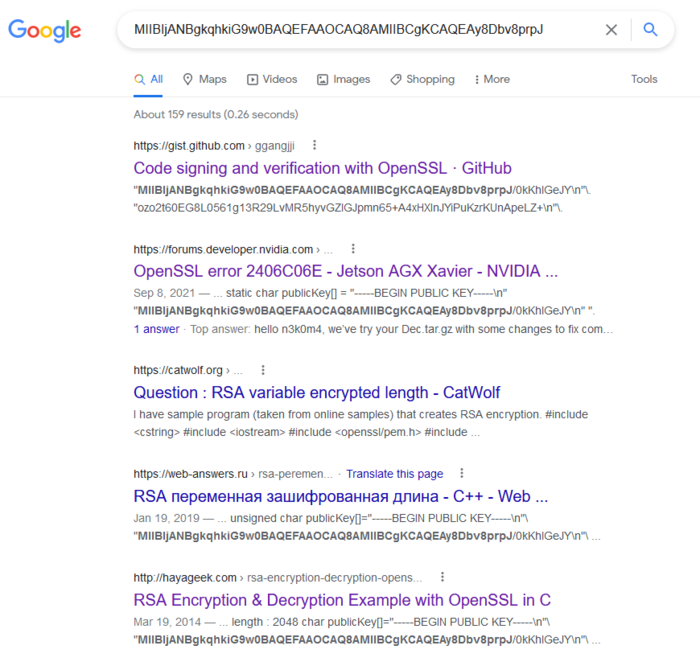
Having received the necessary keys, the researcher was Additionalapplicationsinthefirmware.