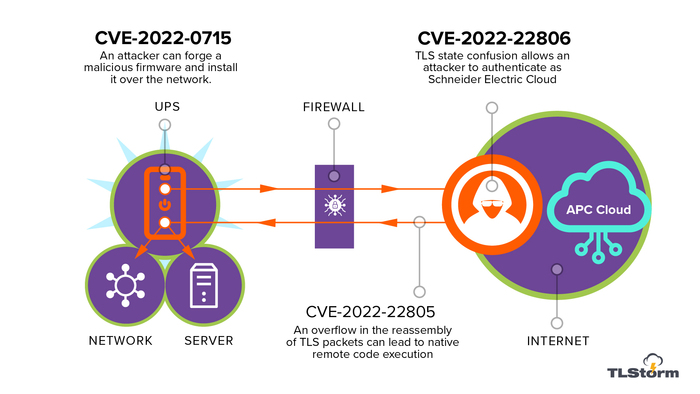
Security researchers from the company Armis revealed Data on Tero vulnerabilities In managed uninterruptible power sources APC, allowing you to remotely get control over the device and manipulate it, For example, turn off the power for certain ports or use as a bridgehead to make attacks to other systems. Vulnerabilities received the TLSTORM code name and affect the APC Smart-UPS devices (SCL, SMX, SRT series) and SmartConnect (SMT, SMTL, SCL and SMX series).
Two vulnerabilities caused Errors in implementing the TLS protocol in devices managed through the centralized cloud service of Schneider Electric. The SmartConnect Series Devices during start-up or loss of the connection are automatically connected to the centralized cloud service and the attacker without authentication can operate vulnerabilities and get full control over the device through sending specially decorated packages.
- CVE-2022-22805 – buffer overflow in the rebeling code of the packets operated when processing incoming compounds. The problem is caused by copying data to the buffer during the processing of fragmented TLS records. Vulnerability operation promotes incorrect error handling when using the Mocana Nanossl library – after returning the error, the connection did not close.
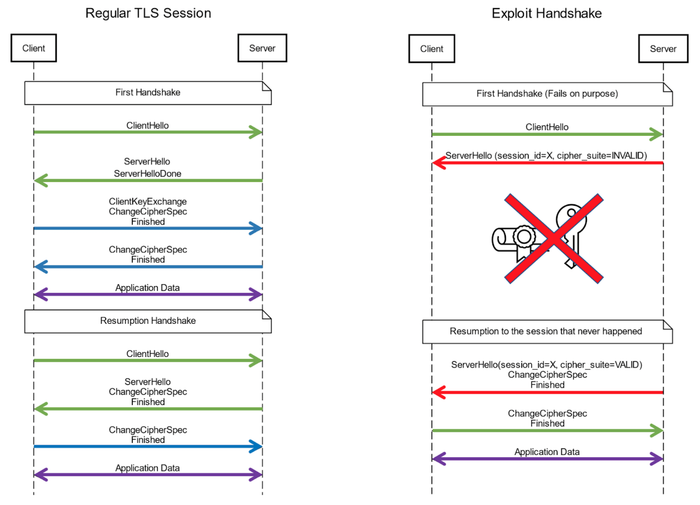
- CVE-2022-22806 – Bypassing authentication when installing a TLS session caused by an error of determining the state when the connection is consistent. The caching of an uninitialized zero TLS key and ignoring the error code returned by the Mocana Nanossl library when the package is received with a blank key, made it possible to pretend to the Schneider Electric server without passing the stage of sharing and check the keys.

Third Vulnerability (CVE-2022-0715) is associated with the incorrect implementation of the test downloadable to update the firmware and allows the attacker to install a modified firmware without testing a digital signature (it turned out that the firmware does not check the digital signature at all, but only uses symmetrical encryption predetermined in firmware key).
In combination with the CVE-2022-22805 vulnerability, the attacker can replace the firmware remotely by issuing himself for the cloud service of Schneider Electric, or initiating an update from the local network. Having access to the UPS attacking can accommodate on the backdoor or malicious code on the device, as well as make a sabotage and turn off the power for important consumers, for example, de-energize the system of video surveillance in banks or life support devices in hospitals.