Researchers from the Defense Scientific and Technical University of the People’s Liberation Army of China, National University of Singapore and the Swiss Higher Technical School Zurich Developed New attack method on insulated Intel SGX enclaves (Software Guard Extensions). The attack was named SMASHEX and caused by reengotic problems when processing exceptional situations during the operation of the Runtime components for Intel SGX. The proposed attack method makes it possible in the presence of control over the operating system to determine the confidential data located in the enclave, or organize copying your code in the memory of the enclave and execution.
The prototypes of the exploits are prepared for enclaves with Runtime based on Intel SGX SDK ( CVE-2021-0186 ) and Microsoft Open Enclave ( CVE -2021-33767 ). In the first case, the possibility of extracting the RSA key used on a Web server for HTTPS is demonstrated, and in the second it was possible to determine the contents obtained by the CURL utility running inside the enclave. The vulnerability has already been eliminated by the software in the issues of Intel SGX SDK 2.13 and OPEN ENCLAVE 0.17.1. In addition to packages Intel SGX SDK and Microsoft Open ENCLAVE Vulnerability also manifests itself in SDK Google Asylo , , Apache Teaclave , rust sgx sdk , SGX-LKL , cosmix and veracruz .
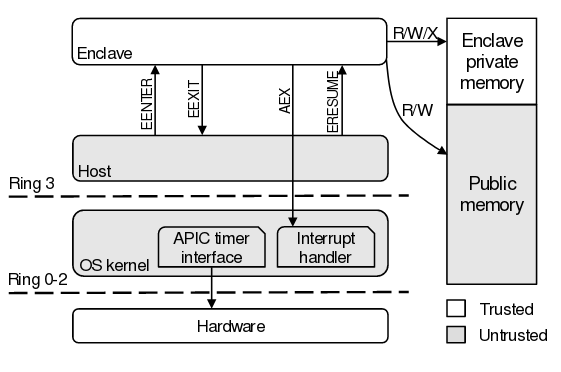
Recall that SGX technology ( Software Guard Extensions ) appeared in the Intel Core processors of the sixth generation (Skylake) and offers a series Instructions that allow you to allocate user-level applications closed memory areas – enclaves whose contents cannot be read and changed even with a kernel and code executed in Ring0, SMM and VMM modes. Transfer the code of code in the enclave is impossible to traditional transition functions and manipulations with registers and stack – for the transfer of control to the enclave, specifically created new Eenter, EEXIT and ERESUME instructions are applied, performing credentials. At the same time, the code was placed in the enclave can apply classical call methods to access the functions inside the enclave and special instructions for calling external functions. To protect against hardware attacks, such as connecting to the DRAM module, encryption of the encryption of the enclave.