Facebook introduced New open static analyzer mariana Trench , aimed at identifying vulnerabilities in applications for the Android platform and Java programs. The possibility of analyzing projects without source texts, for which only Baitcode is available for Dalvik virtual machine. Of the advantages also highlights a very high speed of execution (analysis of several million rows of code takes about 10 seconds), which allows you to strip
Mariana Trench for checking all the changes proposed as they arrive. The project code is written in C ++ and extends under the MIT license.
Analyzer was developed as part of a project to automate the process of reviewing the source text of mobile applications Facebook, Instagram and WhatsApp. In the first half of 2021, half of all vulnerabilities in Facebook mobile applications were detected using automated analysis tools. MARIANA TRENCH code is closely intertwined with other Facebook projects, for example, to paitkode’s parsing, the BajTKode optimizer is used. Redex , and for visual interpretation and study of the results Static Analysis – Library sparta .
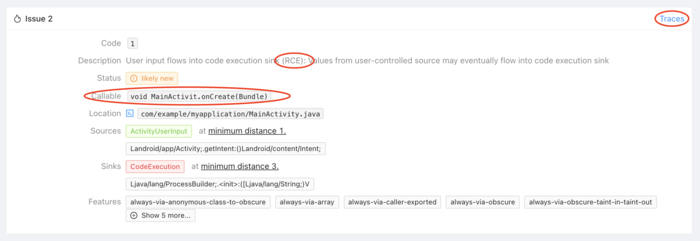
Detection of potential vulnerabilities and confidential problems is carried out by analyzing data streams during the application, which allows you to determine the situation when crude external data is processed in hazardous structures, such as SQL requests, file operations and calls leading to launch external programs.
The analysis of the analyzer is reduced to the definition of data from the receipt of data and dangerous calls in which the initial data should not be used – the analyzer monitors the passage of data on the chain chain of functions and links the source data with potentially dangerous places in the code. For example, the data requested by the Intent.getData call, and the log.w and runtime.exec call as dangerous applications.