Kees Cook (Kees Cook), the former main system administrator Kernel.org and the leader of Ubuntu Security Team, now working in the company Google over ensuring the protection of Android and Chromeos, expressed concern the current error correction process in stable branches of the kernel. Weekly in stable branches are included about one hundred fixes, which is too much and requires large labor costs to accompany the products based on Linux kernel.
In the opinion of Kis, the process of working with errors in the kernel does not pay due attention and the core lacks at least 100 additional developers for coordinated work in this area. The main developers of the kernel regularly correct errors, but there are no guarantees that these fixes will be transferred to the kernel options used by third-party manufacturers. Users of various products based on Linux kernel are also not possible to control what errors are fixed and what core is used in their devices. Ultimately, manufacturers are responsible for the safety of its products, but in the conditions of a very large intensity of the publication of corrections in the stable branches of the kernel, they turned out to be delivered before the choice – to transfer all the corrections, selectively port the most important or ignore all corrections.
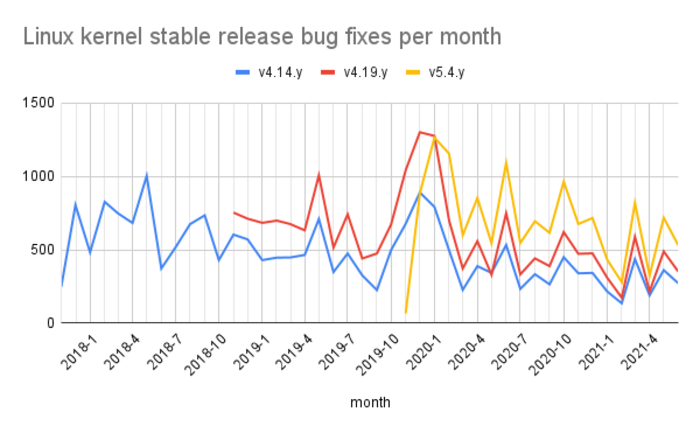
The optimal solution would be to transfer only the most important corrections and vulnerabilities, but in the allocation of such errors from the total flow and is the main problem. The largest number of pop-up problems is a consequence of using the C language, which requires great accuracy when working with memory and pointers. It exacerbates the situation that many potential vulnerabilities are not supplied with CVE identifiers or receive a similar identifier after a while after the correction is published. In such conditions, manufacturers are very difficult to divide secondary corrections from important problems affecting safety. According to statistics, more than 40% of vulnerabilities are eliminated before assigning CVE and on average the delay between the release of correction and the CVE assignment is three months (i.e., the correction is perceived as a normal error, but only a few months later it becomes clear that the elimination of primacy).
In the end, without having a separate branch with corrections of vulnerabilities and not receiving information about the connection with the safety of a problem, manufacturers of products based on Linux kernel remains continuously transferring all fixes from fresh stable branches. But this work requires large labor costs and faces companies with resistance due to concerns in the emergence of regressive changes capable of violating the normal operation of the product.