A group of researchers from Virgin and Califronian universities introduced a new type of attack on the microarchiterate structures of Intel and AMD processors, Detected during the return engineering of undocumented capabilities of the CPU. The proposed Attack method is associated with the use of micro-op Cache intermediate cache processors, which It can be used to extract information that lined up during speculative instructions.
In order to optimize, the processor begins to perform some instructions in speculative mode, without waiting for the previous computing, and if it determines that the prediction was not justified, rolls back the operation to the initial state, but the data processed during the speculative execution is settled in the cache, the contents of which You can define.
It is noted that a new method is noticeably ahead of the performance of the Spectre V1 attack, it makes it difficult to detect the attack and is not blocked by existing methods of protection against attacks by third-party channels, developed to block vulnerabilities caused by speculative instructions (for example, the application of the LFENCE instruction blocks leakage on the latter Stages of speculative execution, but does not protect against leakage through microarchitter structures).
The method affects Intel and AMD processors, manufactured since 2011, including the Intel Skylake and AMD ZEN series. Modern CPU breaks up complex processor instructions on simpler RISC-like micro-operating, which are cached in a separate cache. This cache is fundamentally different from a higher-level cache, is not available directly and acts as a streaming buffer for quick access to the results of decoding CISC instructions in the RISC-microinstruction. Nevertheless, the researchers have found a way to create conditions arising from a conflict of cache access and allow you to judge the content of the micro-operation cache by analyzing the differences in the time of performing certain actions.
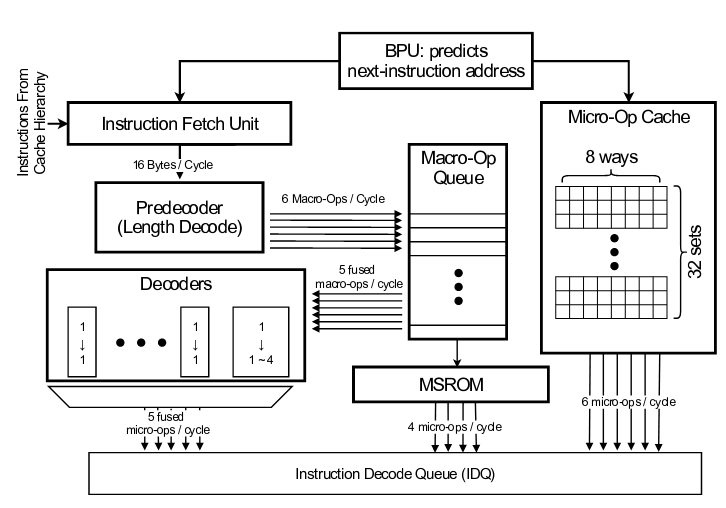
Microelectric cache in Intel processors is segmented in binding to CPU streams (Hyper-Threading), while in the AMD ZEN processors, a common cache is used, which creates conditions for leakage of data not only within a single flux of execution, but also between Different threads in SMT (data is possible between code performed on different logical nuclei CPU).