A group of researchers from several American, Israeli and Australian universities developed three web browsers attacks to extract information about the contents of the processor cache. One method works in browsers without JavaScript, and the other two bypass existing methods of protection against third-party attacks, including those used in the Tor browser and DeterFox … The code to demonstrate the attacks, as well as the server components required for the attacks, are published on GitHub.
To analyze the contents of the cache in all attacks, the Prime + Probe method is used, which implies filling the cache with a reference set of values and detecting changes through measuring the access time to them when re-filling. To bypass the security mechanisms present in browsers that prevent accurate time measurement, in two versions, an appeal is made to a controlled attacking DNS or WebSocket server, on which a log of the request arrival time is kept. In one embodiment, the fixed DNS response time is used as a time reference.
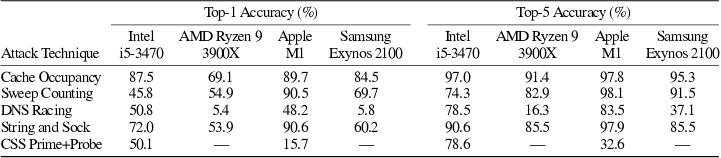
When using a classification system based on machine learning, measurements made using external DNS or WebSocket servers are sufficient to predict values with an accuracy of 98% in the most optimal scenario (on average 80-90%). The attack methods have been tested on various hardware platforms (Intel, AMD Ryzen, Apple M1, Samsung Exynos) and have proven to be versatile.
The first variant of the DNS Racing attack uses the classic Prime + Probe implementation using JavaScript arrays. The differences boil down to the use of an external DNS-based timer and an onerror handler that is triggered when an attempt is made to load an image from a non-existent domain. The external timer allows Prime + Probe attacks in browsers that restrict or completely disable JavaScript timer access.